Web3: Quantum computing danger to blockchain encryption; Shopify NFT integration and marketplace; Cake DeFi proof-of-reserves
Gm Fintech Futurists —
Welcome to our Web3 newsletter, covering DeFi, digital assets, NFTs, and the emergence of the financial metaverse. Today we highlight the following:
DEFI & DIGITAL ASSETS: Cake DeFi Publishes Merkle Tree-Based Proof Of Reserves
CRYPTOECONOMICS & PROTOCOLS: Quantum Computers May Soon Breach Blockchain Cryptography
DAOs, NFTs & Metaverse: Shopify Merchants Can Now Design, Mint And Sell Avalanche NFTs
This content is premium only — give it a share, and leave suggestions in the comments!
DeFi Protocols And Digital Assets
⭐ Cake DeFi Publishes Merkle Tree-Based Proof Of Reserves - Cointelegraph
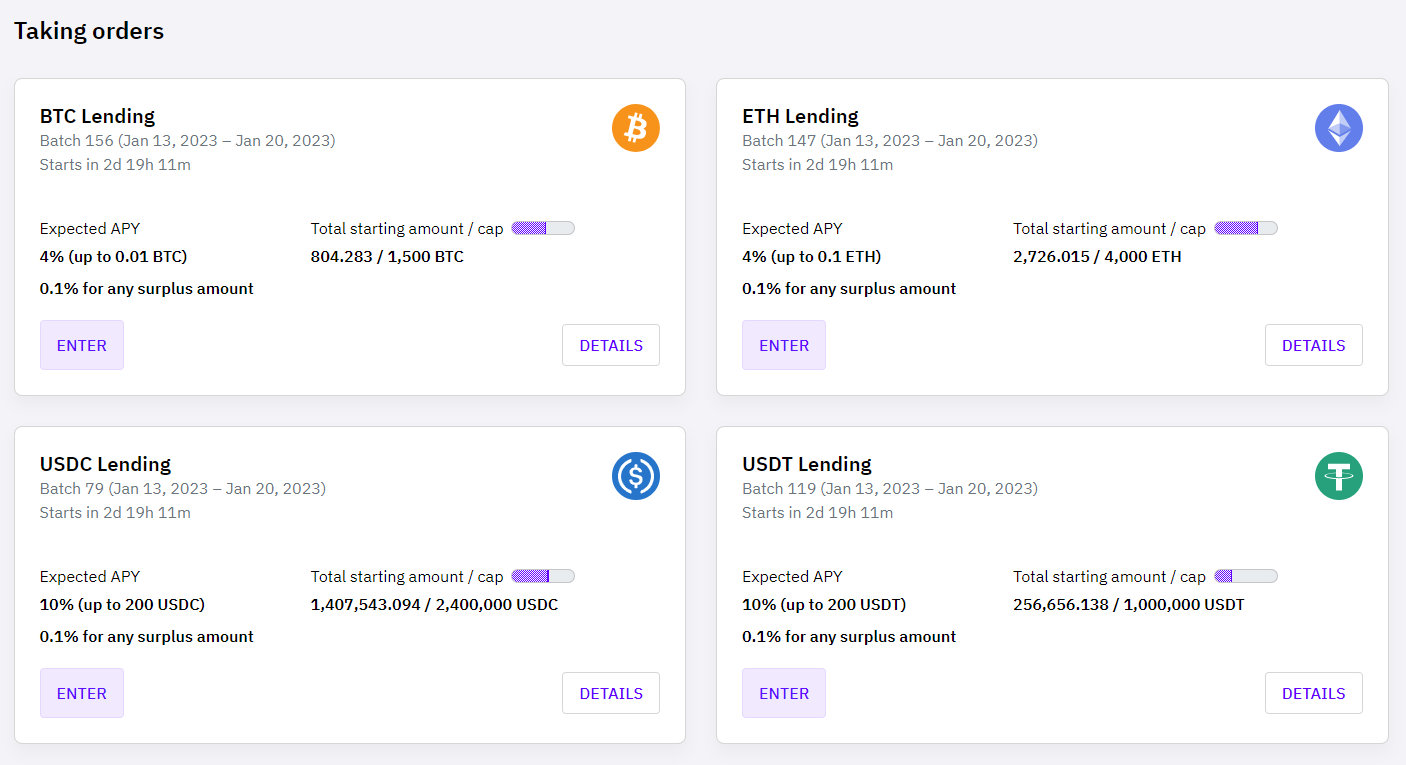
Singapore-based company Cake DeFi, which intermediates user access to DeFi financial products, has launched a publicly accessible Merkle tree-based proof-of-reserve (PoR) feature. Cake DeFi will also show users how yields are generated, with real-time on-chain data about customer funds. You can also seen its lending programs where relevant, though there are still funky practices like offering 10% up to $200, and 0.10% on amounts greater than that.
The company provides (1) Ethereum staking, generating a 4.5% APY; (2) liquidity mining; (3) lending; (4) a freezer, in which you can allocate (freeze) your assets for either staking or liquidity mining shares for a minimum one month to a full ten years. Ten years of staking (lol!) 100 ETH yields 63.3 ETH; and (5) borrowing.
We think it’s great to organize these services in a single platform, but we would prefer such a platform be non-custodial (i.e., like Zerion or Zapper). FTX collapsed by playing games with (i.e., “borrowing”) customer funds, so PoR disclosure is going to be the minimum requirement from companies that straddle custody. Large crypto exchanges like Bybit, Binance, Kucoin, OKX, and Crypto.com have already released some version of their Merkle tree proofs. For context — Ralph Merkle developed the Merkle tree method in 1979. The technique proves that certain data is included in a dataset without revealing the entire data set. Under the PoR method, a Merkle tree is used to verify that an exchange has the reserves it claims to have without disclosing the amount of crypto it holds.
We've touched upon the issues with Merkle-tree PoRs previously. As Chainanalysis mentioned, "Even if you could trace through a centralized exchange, on-chain analysis alone cannot reveal fraudulent intent behind transactions." It’s also possible that blockchain analysis platforms are not incentivized to catch poor on-chain behavior in the first place: "Their customers are the exchanges, and you don't bite the hand that feeds you," according to Bitcoin proponent Samson Mow.
We shouldn’t rely on charity or human nature for safety. Attestation, licensing, and reporting are the requirements in the traditional financial industry when handling clients funds, and custodial services in crypto should be no different.
⭐ Declining Demand For Binance's BUSD Represents New Chapter In Stablecoin Wars - CoinDesk
Lido Rides Liquid Staking Wave To Become Largest DeFi Protocol - The Defiant
Mojo Builds for Hong Kong CBDC - The Defiant
Despite Upstaging Uniswap’s TVL, Curve May Still Not Be Largest DEX - Blockworks
Wallet Associated With Justin Sun Moves $100MM To Huobi - The Block
Balancer Warns $6.3MM Of Funds At Risk, Urges LPs To Remove Liquidity - The Block
Cryptoeconomics And Blockchain Protocols
⭐ Quantum Computers May Soon Breach Blockchain Cryptography - Cointelegraph
Cryptography is all over the news, from zero-knowledge proofs to secure multi-party computation (SMPC) to data encryption. According to a recent paper, "Factoring integers with sublinear resources on a superconducting quantum processor," researchers have showcased a method to break the Rivest-Shamir-Adleman 2048 bit (RSA-2048) signing algorithm, which generates public and private keys. You know — the one present in blockchains and security protocols. RSA-2048 encryption keys are 2048 bits (binary digits) long; factoring would take classical computers an estimated 300 trillion years.
In quantum computing, however, qubits (quantum bits) can be 1, 0, or 1 and 0 simultaneously, meaning that qubits can take on various values simultaneously and perform calculations that a regular computer cannot. Hence, a quantum computer's power grows exponentially in relation to the number of interlinked qubits.